The examples are everywhere: A law firm is tricked into wiring $800,000 into a fraudulent account, and the partners are forced to cover the loss out of their own pockets. A trucking company recently lost $750,000 in the same manner and scrambled to find help to recover the funds. Once the funds are transferred overseas, they are almost impossible to recover.
Business Email Compromise (BEC) is where criminals spoof emails to appear as if they are coming from senior management within the Company. Cybercriminals will often use this scheme to fool employees into wiring funds into an account controlled by hackers. The ploy can often be subtle and difficult to detect when it takes advantage of a legitimate transaction when a spoofed email directs employees at the last minute to send the funds to a different account. Hackers often target law firms, private equity firms, title companies, and CPA firms since they regularly transfer large amounts of funds.
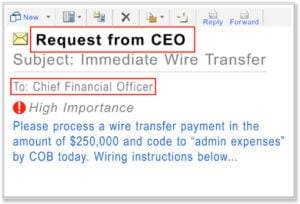
Criminals often rely on specific tactics to perpetrate BEC scams, including:
A false sense of urgency: Cybercriminals (typically posing as attorneys or executives) send spoof emails to victims and convince them to wire money in support of a business deal, such as an acquisition that the victim’s Company is managing. These emails feign urgency or demand secrecy from the victim employee.
A trick domain name: In this instance, victims receive an email asking them to wire money to a specific account. The message originates from a domain that looks credible at first glance, but in fact, has been slightly altered (e.g., one character in the domain name is different). These types of attacks exploit the victims’ lack of attention to sender details.
Impersonation of a vendor: This type of cyber attack involves emails impersonating one of the Company’s vendors. The sender’s domain name is genuine, and the transaction seems legitimate—often with proper documentation attached—because the scammer has hacked into the vendor’s email account. However, the processing details direct payment to an account that the criminal controls.
So, what can your firm do to prevent these fraudulent transfers? Some basic countermeasures will significantly reduce the risk to your firm:
-
Flag external emails: Set your email service to flag emails that originate from outside your organization. Spoofed emails will show an internal email on the “From” line that the user views, but your email service reads the extended header, showing where the message originated. Emails that are flagged as external but show an internal email address should be treated with suspicion.
-
Define what transactions require scrutiny: Regular transactions to the same party probably don’t need to be verified each time. Changes such as account number or significant deviation from the normal amount should require additional checks.
-
Define the firm’s authorizing officials: Only certain managers within the firm should be designated to authorize wire transactions and up to a preset amount. Any “out of bounds” transactions should be subject to additional verification.
-
Implement multi-step verification procedures: For transactions above a certain level or involving bank/account number changes, employees should not rely only on emailed instructions. Require employees to call the authorizing official and verify the transaction. Do not rely on any phone number included in the email; use the Company’s internal directory.
-
Train your staff and develop security awareness: Verification processes will only work if employees are trained appropriately and implement them daily. Make sure your staff is aware of the threat of business email compromise, the tricks commonly used by cybercriminals, and the firm’s processes to prevent fraudulent funds transfers. Your employees are your first line of defense!
If you need a cybersecurity training program developed to educate your staff, please contact Bawn
.png?width=230&height=66&name=Logo%20Transparency-1%20(1).png)
.jpg?width=520&height=294&name=Shutterstock_1803527689%20(4).jpg)

.png?width=110&height=110&name=ancient-scroll%20(1).png)
Comments