Tags:
Security Best Practices, Cybersecurity for Small Businesses and Startups, Security Awareness and TrainingWhen discussing Cybersecurity, often a firm executive will say, “Oh, we have an IT person/ department/ firm who handles that, and they’re really good.” Information Technology and Cybersecurity both deal with technology, but they are not the same and require different skill sets to be conducted effectively.
Information Technology (IT) allows your to streamline work processes and improve communication within the company, thereby helping your employees save time and making your operations much more efficient. The focus is on making information quickly available to each employee when they need it. Various technologies are incorporated and maintained to make this happen, from laptops to servers to cloud-based storage.
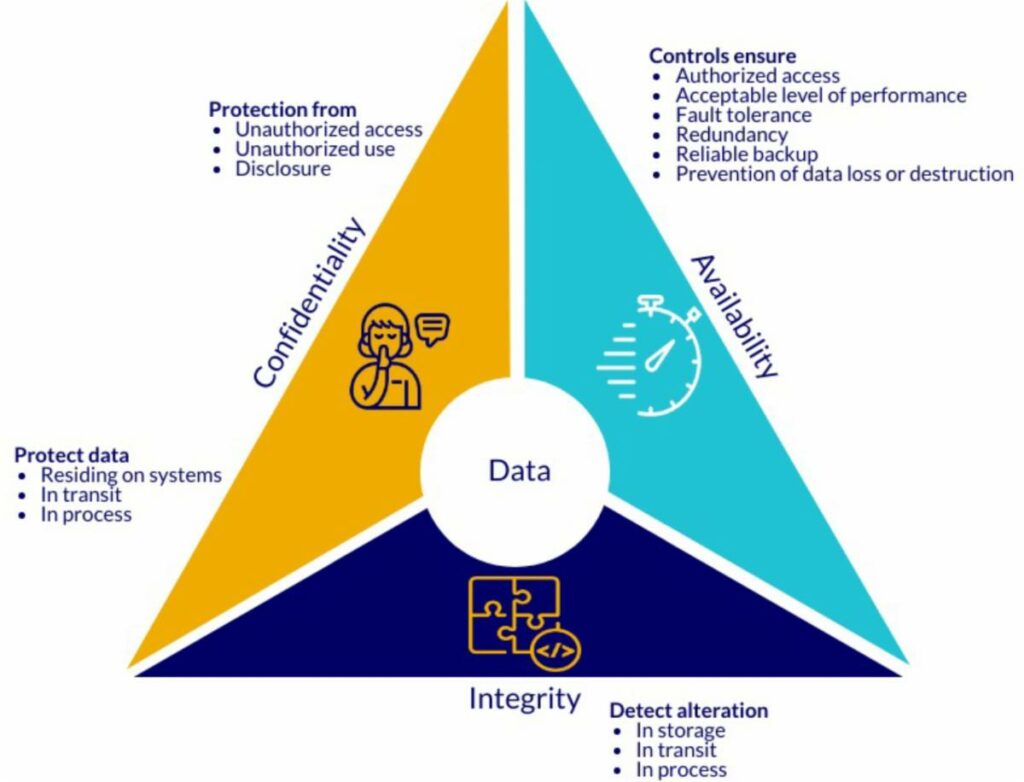
The objective of Cybersecurity is to prevent or mitigate harm to—or destruction of—the firm’s information technology infrastructure and data. The focus is on ensuring that a firm’s information remains confidential and unaltered. Effective Cybersecurity involves people, processes, and technology.
88% of cybersecurity breaches are caused by human error. 94% of malware is delivered via email. Phishing attacks account for more than 80% of reported security incidents. With statistics like these, it is clear that employees of any firm play a very large role in securing its data. In fact, security awareness training provides the most significant return on investment of any type of cybersecurity solution.
Appropriate plans and policies are vital to maintaining effective Cybersecurity. To guide employee behavior and develop a meaningful security culture, leadership needs to determine what is expected and set the tone for all levels of the company to follow. Below are some example questions that should be answered when developing security policies:
-
What does leadership consider to be an acceptable risk?
-
What is appropriate behavior for employees?
-
How are accesses handled when an employee leaves the company?
-
What steps should be taken before sharing confidential information with an outside entity?
-
What are the steps to be taken if a data breach occurs?
We have seen repeated instances where companies will spend large amounts of money for a technology solution, which is placed into the company’s network. However, the time isn’t taken to configure the solution to the unique characteristics of the company’s system, and employees aren’t trained on the solution. A misconfigured or unused solution provides no real security gain. Real gains in security are only made when a thoughtful strategy is developed, and policies, training, and technology are then brought in to support the strategy.
If you need help with an effective cybersecurity strategy that involves people, processes, and technology, please call Bawn.
.png?width=230&height=66&name=Logo%20Transparency-1%20(1).png)


.png?width=110&height=110&name=ancient-scroll%20(1).png)
Comments