Cybersecurity centers around the use of technology, but it is not an issue that can be addressed solely by a company’s Information Technology (IT) department. The potential impact of a cyber incident is too significant and requires leadership and awareness from the top of the organization. When Colonial Pipeline was hacked, the company paid a $4.4 million ransom. Some of this money was later recovered, but the attack has cost Colonial Pipeline in other ways.
The company supplies approximately 45% of fuel to the East Coast and elected to shut down operations during the attack, affecting millions of customers with a spike in gasoline prices. Fearing gas shortages due to social media and news hysteria, nervous motorists waited in line at gas stations for hours in some areas. The following month, CEO Joseph Blount was called to testify before the Senate Committee on Homeland Security and Government Affairs. Once an obscure part of industrial infrastructure, Colonial Pipeline is now widely recognized as a ransomware victim, exposing the frailties of critical infrastructure to cyber-attacks.
The American Medical Collection Agency (AMCA) was a debt and medical receivables collection agency focused on collecting patient receivables for various third-party clinical-diagnostic laboratories. AMCA collected and maintained PII on millions of patients during normal business operations, including names, home addresses, Social Security numbers, and bank account and credit card information. AMCA invested over $1 million to upgrade its IT systems, but this did not prevent a significant data breach in 2019. After disclosing this cyber-attack, major clients, including Quest, Labcorp, and others, opted to terminate business with AMCA. In addition to the immediate revenue impact, AMCA began to incur significant costs resulting from the breach, including litigation and remediation. AMCA lacked cyber liability insurance, and the company covered the costs through a $2.5 million loan and company cash. AMCA also sought costs savings through a 75% reduction in headcount. Three months later, AMCA filed for bankruptcy, and the company was eventually dissolved.
The impact of a cyberattack quickly spills beyond the Information Technology (IT) space, and a company’s top leadership needs to address cybersecurity as part of its overall risk management strategy. This holds true both from a risk mitigation approach before a cyber incident occurs and navigating the company through crisis when a major cyber-attack occurs.
What is your organization’s cyber risk?
A cyber risk appetite statement explicitly defines what an organization has deemed an acceptable risk, and every organization’s risk tolerance will be different. This statement should be unambiguous and measurable to enable strategic decision-making for the organization’s leadership.

Set your risk appetite in three steps
Step 1 – Identify the loss event types that are most relevant
A risk appetite may not represent a single value for every type of cyber event. It may be defined differently for each (or at least derived differently). Focus on the types of loss that are most relevant to your organization.
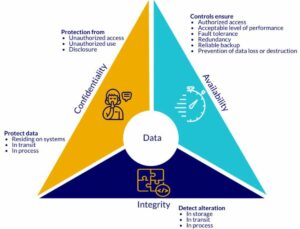
The three types of loss experienced in the cybersecurity space are commonly related to the CIA triad (Confidentiality, Integrity, and Availability). Consider these data issues when identifying events that would have the most impact.
Step 2 – Define thresholds for “unacceptable” loss exposure
Some organizations may not know what this “unacceptable” dollar value may be during the first pass. This is why it is important to use open questions to drive the discussion around risk appetite. Rather than directly asking for risk appetite, develop a list of questions to help guide the discussion, such as:
-
What monetary values will impact an organization’s financial reporting?
-
What is our current cyber insurance coverage?
-
What are the most significant security and availability events that have happened at our organization? What was the impact?
-
What is the maximum duration of an outage for our critical systems that we are willing/able to withstand?
-
What is the maximum number of confidential records we are willing to accept being breached?
Step 3 – Validate risk appetite values using a sample of quantitative risk scenarios and obtain buy-in
Once an initial risk appetite value has been established, it’s important to benchmark this figure and obtain buy-in from key stakeholders. The diagram below shows the results (using notional values) of the established risk appetite for confidentiality-related risk scenarios compared to the top five cyber risks identified by an organization.
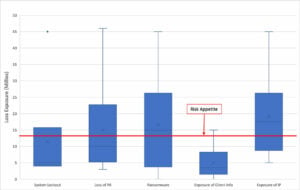
Each blue box indicates where the majority (80%) of the results of the simulated risk scenarios were contained (the whiskers represent the outliers). If we focus on the 80%, then the results indicated that four of the top five risks had loss exposures that exceeded the organization’s risk appetite. At this point, a decision on whether to invest in additional resources should be analyzed to determine if the amount of the risk reduction in dollars and cents justifies the investment cost.
If you need to develop a cyber risk strategy, call Bawn at 888-477-2296.
.png?width=230&height=66&name=Logo%20Transparency-1%20(1).png)


.png?width=110&height=110&name=ancient-scroll%20(1).png)
Comments